Cloud computing and virtualisation are becoming increasingly important. But does this mean that the future lies exclusively in the cloud? We are convinced that in most cases hardware will continue to play an important role. However, it can also be optimally supplemented by virtual machines and computers, which can be remotely accessed via network protocols, to create hybrid infrastructures. One part of IT structures will still be present, while the other part is available virtually via cloud computing.
But how can you link such hybrid structures as flexibly as possible? How do you standardize their use so that operators can handle them easily, efficiently and in line with their needs? The RemoteAccess-CPU is your solution.
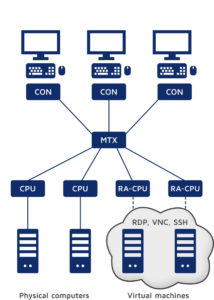 How does the RemoteAccess-CPU work?
How does the RemoteAccess-CPU work?
The RemoteAccess-CPU lets you seamlessly integrate virtual machines into KVM matrix installations. The modules establish a connection between matrix systems and computers or virtual machines, which can be remotely accessed via network protocols (RDP, VNC and SSH). This way, you can optimally implement hybrid systems with real and virtual computer infrastructure. After appropriate configuration, you can access any number of virtual sources and computers accessible via network protocols directly via KVM matrix systems – uniformly and exactly as you would access computers under your desk.
A KVM installation with a dedicated CPU for remote access has significant advantages
Why would you need a special CPU to access a virtual target, if e.g. an IP-CON is already working in the network? Basically, you could also use a CON for accessing a target. However, only a special CPU lets you benefit from the full matrix integration and the advantages it offers. This is where the use of a RemoteAccess-CPU comes in handy.
Simply select the desired source from a standardized select menu (target list) on the on-screen display – regardless of whether the computer is available in the server room, via network protocol or in the cloud. The KVM matrix controls the logic and takes over user administration. Since we attach great importance to security, all connection data is forwarded in encrypted form.
Benefit from hands-on KVM functions even in hybrid systems
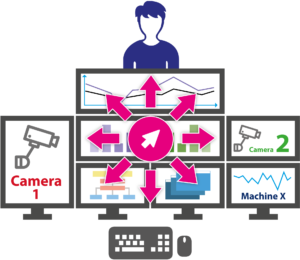 When working with several computers at the same time, you can use CrossDisplay-Switching, for example, regardless of whether you work on physical or virtual machines. CrossDisplay-Switching lets you switch between sources quickly and easily using the mouse. When the mouse pointer moves from one monitor to another, the keyboard-mouse focus automatically switches to the corresponding computer. This feature therefore lets you create multi-monitor workplaces, where operators do not have to deal with the infrastructure used in the background. They simply perform their tasks while operating the system intuitively.
When working with several computers at the same time, you can use CrossDisplay-Switching, for example, regardless of whether you work on physical or virtual machines. CrossDisplay-Switching lets you switch between sources quickly and easily using the mouse. When the mouse pointer moves from one monitor to another, the keyboard-mouse focus automatically switches to the corresponding computer. This feature therefore lets you create multi-monitor workplaces, where operators do not have to deal with the infrastructure used in the background. They simply perform their tasks while operating the system intuitively.
The push-get function is also available in such an application. It facilitates cooperation in control rooms and lets users move the screen contents of their monitors to (push) – or get it from – the display of another console. This display can be a large screen projection, for example. This solution also improves communication, flexibility and speed within the team, as employees can now perform tasks together.
Integrated thin client functionality and multi user access
The RemoteAccess-CPU provides a powerful, reliable industrial board and offers a platform with integrated thin client functionality. Therefore, you don’t need a separate thin client – and the solution is highly integrative when it comes to establishing connections.
Via G&D‘s KVM system, multiple operators can use the same RemoteAccess-CPU to simultaneously connect to and operate the same virtual machine.
Pooling function: an additional option for a better and secure workflow
Connecting to a target requires one RemoteAccess-CPU for each target. Thanks to multi-user access, several operators can use this connection at the same time. If an operator wants to access another target, a “free” RemoteAccess-CPU is automatically used in standard mode. This works as long as the targets run in the same network.
When using multiple separate networks (for example, one network for general access and one network for specially secured access), you need at least as many RemoteAccess-CPUs as networks. Now, you can connect a RemoteAccess-CPU to each network to establish a connection to a target in this network.
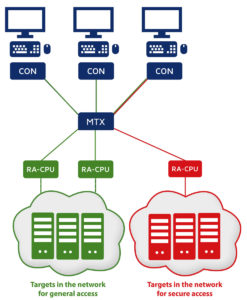 Let’s take a look at an example: You are using two separate networks. One network is generally accessible. The second network is specially secured, but authorized staff have to be able to access it at all times. In addition, you have RemoteAccess-CPUs.
Let’s take a look at an example: You are using two separate networks. One network is generally accessible. The second network is specially secured, but authorized staff have to be able to access it at all times. In addition, you have RemoteAccess-CPUs.
For this kind of installation or application, you can use the pooling function. During configuration, you assign each RemoteAccess-CPU to a network. In the example, two RemoteAccess-CPUs are assigned to the generally accessible network and one device to the specially secured network. This has the big advantage that you always have a free RemoteAccess-CPU to connect to a target in the secured network, which guarantees access for authorized staff.
SCN names RemoteAccess-CPU Product of the Year 2020
Functionalities such as pooling and multi-user access ensure that the RemoteAccess-CPU is ideal for integrating virtual sources. Every year, the trade publication SCN – System Contractor News identifies the most effective products for the AV industry. We are proud that the RemoteAccess-CPU has been named SCN Product of the Year 2020.
- TOP 100 innovators – G&D among Germany’s most innovative mid-sized companies - 18. February 2021
- RemoteAccess-CPU – how to integrate virtual machines into your KVM matrix installation - 10. December 2020
- Key sets: how to operate your KVM installation even easier and faster - 17. September 2020

