A common argument against KVM-over-IP systems is that network-based transmission is less secure than the direct connection used in classical systems. This argument is often based on the belief that network connections are more vulnerable to attacks, and therefore pose a higher security risk. In this blog post, we aim to explore this topic and dispel the myth that KVM-over-IP systems are inherently less secure than their classical counterparts.
KVM-over-IP
What is KVM-over-IP? In a KVM-over-IP system, data packets are transmitted over Ethernet networks (OSI model Layer 2), while the communication is based on IP (Layer 3). In a classical KVM system, the connection is made through dedicated cables (Layer 1 – Physical Layer), enabling direct communication between the operator and the target computers.
Does the use of IP-based transmission increase the security risk, and how can effective protection against external cyber threats or internal threats via network access be ensured? Our KVM-over-IP solutions offer a variety of security features that enable you to control and secure access to the managed computers. These include, among others:
Encryption
When connecting devices to an IP matrix, data transmission is encrypted, for instance, through a VPN tunnel. G&D utilizes two separate ports in its KVM-over-IP systems for transmitting all critical data within the IP network. Communication between the operator and the target computer is consistently protected by AES-256 encryption to ensure that unauthorized access is prevented. The bootloader, operating system, and firmware of the IP matrices together form a “Trusted Computing Platform,” which protects the system from third-party tampering. An integrated “Trusted Platform Module” (TPM hardware module) uses RSA encryption with a 2048-bit key to secure all access and configuration data from unauthorized access. Additionally, highly sensitive information, such as login data and passwords, is permanently stored in encrypted form. Any modification to the firmware is detected early, resulting in the boot process being aborted to prevent potential threats.
Authentication
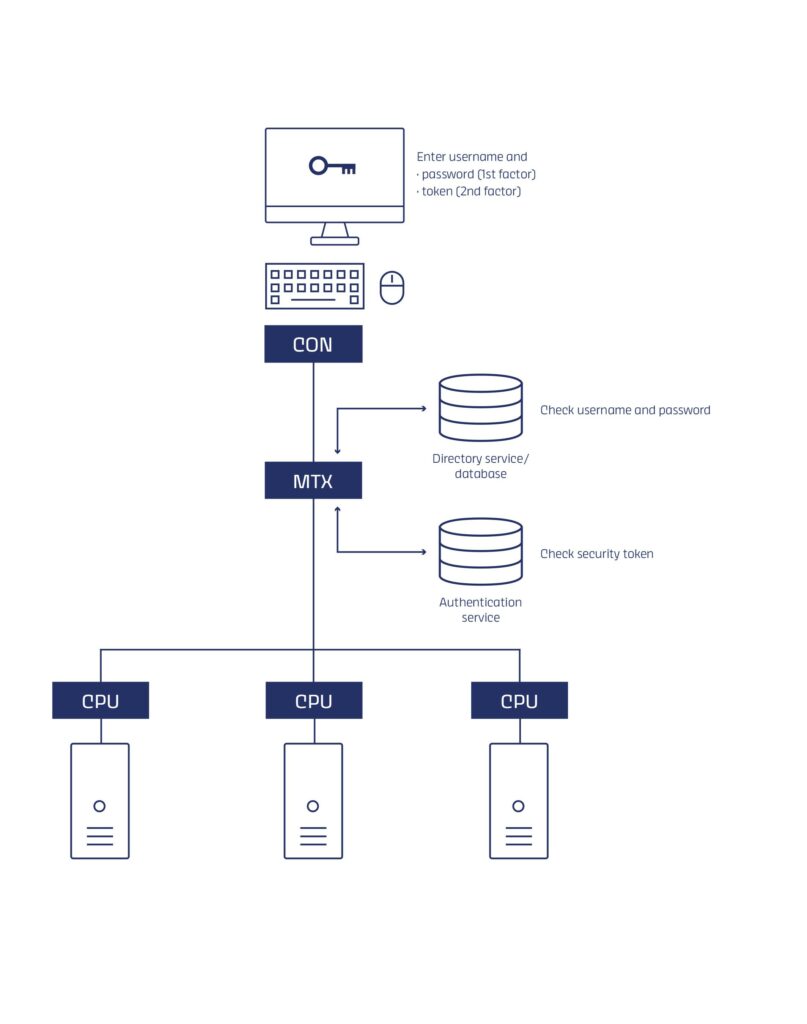
To ensure that only authorized users can access the managed computers, our KVM-over-IP solutions support various authentication methods. In addition to user authentication via password, an optional Two-Factor Authentication (2FA) can be implemented to add a second possession-based factor for enhanced security. This utilizes a Time-Based One-Time Password (TOTP), which is valid for a limited time and can only be used once. Depending on individual requirements and preferences, two-factor authentication can be carried out using either authenticator apps or hardware tokens. Users also have the flexibility to choose whether they want to use the device’s internal authentication server or an external directory service, such as LDAP, Active Directory, RADIUS, or TACACS+.
Access control
The use of KVM systems to offload computer systems offers significant advantages, especially in terms of the physical security of IT systems. By using KVM systems, administrators can physically separate the computers from users’ workplaces. This means that the actual servers and computers are housed in a secure, centralized room, while users access these systems remotely via IP-KVM systems. Administrators can configure access rights by determining which users or user groups are allowed to access specific computers or servers. This is done through the assignment of specific permissions and profiles, ensuring that each user only gains access to the systems for which they are authorized. This level of control greatly enhances security by preventing unauthorized individuals from gaining physical access to critical IT resources.
UID-Locking
This security feature allows for the definition and control of a specific pool of devices belonging to a particular KVM installation. UID Locking ensures that only authorized (KVM) devices within this pool can be used. This prevents the addition of new or replacement devices, enhancing the integrity and security of the system. In addition to restricting access to specific devices, USB 2.0 data connections can also be disabled. This means that no data transfers can occur via USB 2.0 ports, further reducing the risk of unauthorized data access or transfers.
Forward/Backward Security
A unique feature of our devices is the forward/backward security for generating new security keys. When a workplace module connects to a computer module, a security key is generated for that connection. If another workplace module connects to the same computer module, both workplace modules receive new security keys to ensure all connections remain optimally protected. Similarly, when one module disconnects, a new security key is sent to the remaining workplace module. This dynamic key management ensures maximum security. The continuous updating of security keys is a distinctive feature of G&D devices, ensuring that every connection is individually secured. This minimizes the risk of unauthorized access and guarantees the integrity of the entire IT infrastructure.
Security Certifications
With our new SecureCert feature, our KVM-over-IP systems meet stringent security certifications that comply with the high requirements of security-critical environments. The listing of our systems on the DoDIN APL (Department of Defense Information Network Approved Products List) confirms that our solutions are approved for use in U.S. Department of Defense networks. The Common Criteria EAL2+ (Evaluation Assurance Level 2+) ensures an independent security evaluation based on international standards. Additionally, the FIPS 140-3 (Federal Information Processing Standard) certification guarantees that our systems meet strict cryptographic requirements. These external validations confirm the high security of our IP solutions and enable their use in security-critical and regulated environments such as government agencies, the military, and highly sensitive industrial applications.
Conclusion
When all these security features are properly configured and applied, KVM-over-IP can be utilized as securely as classical KVM systems. The ability to centrally control and monitor access to managed computers using a KVM system provides an additional security advantage. Of course, it is essential to consider the best security practices when implementing KVM-over-IP and to regularly perform security updates to address potential vulnerabilities. However, it is fundamentally incorrect to assume that KVM-over-IP is inherently less secure than classical KVM systems. With the right security measures in place, KVM-over-IP can be a secure and powerful alternative that offers many benefits.
How can KVM-over-IP be deployed securely and efficiently in critical environments?
Our white paper “Secure KVM solutions: KVM-over-IP™ matrix systems for mission-critical applications” offers an in-depth look. It presents how the systems work, their benefits, expert knowledge, and best practices.
>> Other articles you might be interested in:
SecureCert: New Feature for Mission-Critical Infrastructures
Classic KVM vs. KVM-over-IP – a comparison
- Built for Live Sports Arena Operations: How KVM Supports Game Day Performance - 12. February 2026
- G&D and VuWall honor outstanding partners at ISE 2026 - 5. February 2026
- Future-Proof Control Rooms: STADLER SYSTEC Relies on G&D Solutions - 30. January 2026


