With “Managing Trust” as keynote theme, this year’s CeBIT focuses on the topics trust and security in the digital age. According to CeBIT, “the greater the trust in the solutions and applications of the international ICT industry, the faster the global economy can grow.” But privacy, technical security and the reliability of systems still remain to be main concerns for both economy and users.
As a manufacturer of KVM products, we are deal with these concerns on a daily basis. By being able to access numerous computers at the same time, security is of paramount importance when it comes to developing and manufacturing KVM products. When I heard the CeBIT keynote theme, I immediately thought about what “Managing Trust” actually means for KVM.
By taking a closer look at how KVM can be applied in air traffic control, I will show you in three steps how KVM products help creating a secure working environment for controllers. How can KVM be applied to make sure that the monitors in the tower will not suddenly turn blank? And how does it help preventing system failures?
1. Removing computers from the tower
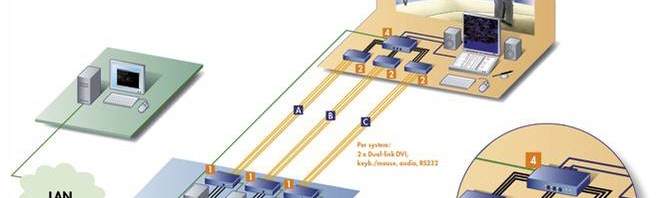
 If you ever had the chance to visit a tower at an airport or simply watched a movie giving you an idea of how they look like, you might have a pretty good idea of how packed these places can get. To provide air traffic controllers with more space, it is therefore useful to remove any computers from the tower into a separate server room. Now they can stretch their legs and are even able to work without being distracted by heat, noise or maintenance staff. But how can they access their computers if they are placed in a remote server room? That’s exactly where KVM comes into play. KVM extenders are the key for connecting the computers in the server room and the tower. Even over great distances, optical fibres transmit computer signals such as keyboard, video, mouse, audio or USB 2.0 in real time and without any loss in quality to the screens of the controllers.
If you ever had the chance to visit a tower at an airport or simply watched a movie giving you an idea of how they look like, you might have a pretty good idea of how packed these places can get. To provide air traffic controllers with more space, it is therefore useful to remove any computers from the tower into a separate server room. Now they can stretch their legs and are even able to work without being distracted by heat, noise or maintenance staff. But how can they access their computers if they are placed in a remote server room? That’s exactly where KVM comes into play. KVM extenders are the key for connecting the computers in the server room and the tower. Even over great distances, optical fibres transmit computer signals such as keyboard, video, mouse, audio or USB 2.0 in real time and without any loss in quality to the screens of the controllers.
2. Establishing a monitoring system
 But, of course, simply removing computers from the tower doesn’t prevent the systems from failing. To avoid failures, applying a monitoring system based on hardware comes in handy. The system, which is implemented in each KVM extender, monitors all system statuses of any connected extender lines, detects statuses that might lead to failures (according to defined thresholds, e.g. temperature) and sends an SNMP trap to the IT warning them about said status.
But, of course, simply removing computers from the tower doesn’t prevent the systems from failing. To avoid failures, applying a monitoring system based on hardware comes in handy. The system, which is implemented in each KVM extender, monitors all system statuses of any connected extender lines, detects statuses that might lead to failures (according to defined thresholds, e.g. temperature) and sends an SNMP trap to the IT warning them about said status.
By actively monitoring all extender lines and thanks to redundant components within the applied KVM extenders, IT and controllers are able to detect possible failures before they even occur.
3. Implementing primary, redundant and fallback systems
 To make entirely sure the systems won’t fail despite being monitored, two additional connections, a redundant and a fallback system, are implemented. In case of a system failure, controllers now have access to two other active systems, because all three systems are connected to the KVM switch placed at the controller’s desk. Now you might ask yourself how controllers can be sure the additional systems are active and will work properly. That’s simple: since all three systems are connected to the KVM switch, they are all monitored. Again, any possible failures are reported via SNMP trap. And just like that KVM makes sure that controllers always have an active system helping them monitor the air traffic.
To make entirely sure the systems won’t fail despite being monitored, two additional connections, a redundant and a fallback system, are implemented. In case of a system failure, controllers now have access to two other active systems, because all three systems are connected to the KVM switch placed at the controller’s desk. Now you might ask yourself how controllers can be sure the additional systems are active and will work properly. That’s simple: since all three systems are connected to the KVM switch, they are all monitored. Again, any possible failures are reported via SNMP trap. And just like that KVM makes sure that controllers always have an active system helping them monitor the air traffic.
Another advantage of these three steps: By combining optimised working environments, an active monitoring system and three independent extender lines, controllers will never have to worry about their systems, can work highly concentrated and will always keep their cool. And you might want to have a concentrated air traffic controller if you are on that aeroplane taking you to your well deserved holidays.
What do you think about security and trust in the applications of the ICT industry? What does “Managing Trust” mean to you?
- Trade shows 2023: Experience G&D KVM products live and up close - 11. January 2023
- Innovative KVM solutions for control rooms - 14. December 2022
- Ada Lovelace – a true visionary and the world’s first female programmer - 12. December 2022

Thank You so much for your information.